Network Virtualization Using GRE – Cisco Network Virtualization
Network Virtualization Using GRE
NVGRE (Network Virtualization using Generic Routing Encapsulation) is a network virtualization method that creates virtual Layer 2 topologies on top of a physical Layer 3 network. Connectivity in the virtual topology is provided by tunneling Ethernet frames in GRE over IP over the physical network. The purpose is to enable multitenant and load-balanced networks that can be shared across on-premises and cloud environments. NVGRE protocol was proposed by Microsoft and its partners as part of the Hyper-V solution. Hyper-V is Microsoft’s hardware virtualization solution, similar to VMWare’s ESXi solution.
In NVGRE, every virtual Layer 2 network is associated with a 24-bit identifier, called a virtual subnet identifier (VSID). A 24-bit VSID supports up to 16 million virtual subnets in the same management domain, in contrast to only 4094 achievable with VLANs. Thus, NVGRE solves the problems caused by the limited number of VLANs the IEEE 802.1Q specification enables, which is inadequate for complex virtualized environments and makes it difficult to stretch network segments over the long distances required for dispersed data centers. To support a multi-subnet virtual topology, data center administrators can configure routes to facilitate communication between virtual subnets of the same tenant. NVGRE leverages the GRE header to carry VSID information in each packet.
NVGRE endpoints (NVEs) are the ingress/egress points between the virtual and the physical networks. Any physical server or network device can be an NVGRE endpoint. One common deployment is for the endpoint to be part of a hypervisor. The primary function of this endpoint is to encapsulate/decapsulate Ethernet data frames to and from the GRE tunnel, ensure Layer 2 semantics, and apply isolation policy scoped on VSID. The endpoint can optionally participate in routing and function as a gateway in the virtual topology. To encapsulate an Ethernet frame, the endpoint needs to know the location information for the destination address in the frame. This information can be provisioned via a management plane or obtained via a combination of control-plane distribution or data-plane learning approaches.
Figure 7-4 shows the NVGRE frame format.
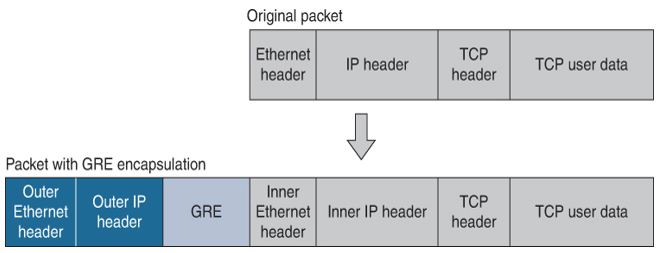
Figure 7-4 NVGRE Frame Format
- Outer Ethernet header: The source Ethernet address in the outer frame is set to the MAC address associated with the NVGRE endpoint. The destination endpoint may or may not be on the same physical subnet. The destination Ethernet address is set to the MAC address of the next-hop IP address for the destination NVE.
- Outer IP header: The IP address in the outer frame is referred to as the Provider Address (PA). There can be one or more PAs associated with an NVGRE endpoint, with policy controlling the choice of which PA to use for a given Customer Address (CA) for a customer VM.
- GRE header: In the GRE header, the C (Checksum Present) and S (Sequence Number Present) bits must be 0 and the K (Key Present) bit must be set to 1. The 32-bit Key field in the GRE header is used to carry the VSID and the Flow ID. Flow ID is an 8-bit value that is used to provide per-flow entropy for flows in the same VSID and must not be modified by transit devices. If FlowID is not generated, it must be set to all zeros. The protocol field in the GRE header is set to 0x6558.
- Inner Ethernet and IP header: The inner Ethernet frame is composed of an inner Ethernet header followed by optional inner IP header, followed by the IP payload. The inner frame could be any Ethernet data frame, not just IP. The IP address contained in the inner frame is referred to as the Customer Address (CA).
Figure 7-5 shows a typical NVGRE communication. The traffic is transported from VM1 (10.0.0.5) to VM2 (10.0.0.7). Two VM1s with the same IP address are representing two different customers using the same IP address space. The original IP packet is encapsulated with the MAC header containing MAC addresses of the source and destination VMs of specific customer VMs that are communicating. On top of that, a GRE header is added that contains a VSID used to identify each virtual network. The outer IP header contains the source and destination IP address of the tunnel endpoints (that is, the provider address).
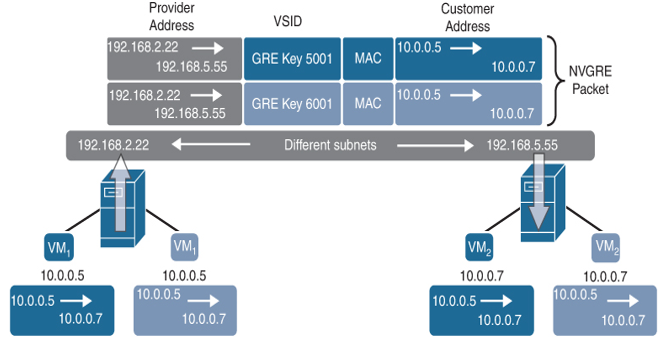
Figure 7-5 NVGRE Communication